I am text block. Click edit button to change this text. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Web Application Penetration Testing
Web Application Penetration Testing
Infrastructure Penetration Testing
API Security Testing
Mobile App Penetration Testing
Thick & Thin Client Testing
Phishing Simulation
Wireless Penetration Testing
Database Penetration Testing
OT Hacking
Radio Hacking
Red Team Exercise
Hardware Hacking
Phirautee- Writing Ransomware using Living off the Land (LotL) Tactics
Ransomware va-user todayApril 24, 2019 184 92 3

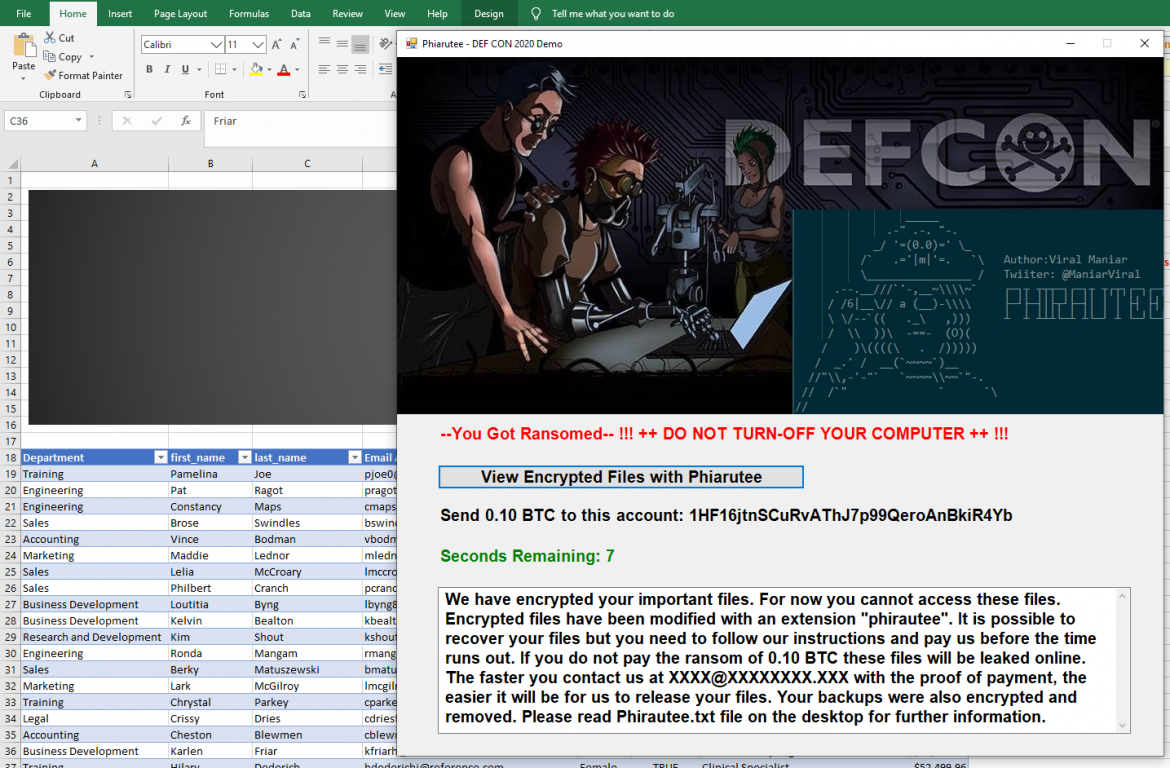
Over the past few years, ransomware has gone wild and organisations around the world are getting targeted leading to the damage and disruption. As we all know that the threat landscape is changing rapidly and we hear the fuss about ransomware infection at the offices or read about it in the news. Have you ever wondered how threat actors are writing ransomwares? What level of sophistication and understanding is required to target an organisation? In this demo, we will utilise the native Windows commands to build ransomware and target a host via phishing. Introducing Phirautee, a proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written purely using PowerShell and does not require any third-party libraries. This tool steals the information, holds an organisation’s data to hostage for payments or permanently encrypts/deletes the organisation data. The tool uses public-key cryptography to encrypt the data on the disk. Before encrypting, it exfiltrates the files from the network to the attacker. Once the files are encrypted and exfiltrated, the original files are permanently deleted from the host and then tool demands a ransom. The ransom is asked using the cryptocurrency for payments, so transactions are more difficult for law enforcement to trace. During the demonstration of Phirautee, you will see a complete attack chain i.e. from receiving ransomware attack via a phishing email and how the files get encrypted on the compromised systems. A detailed walk-through of the source code would be provided to understand how hackers utilise simple methods to create something dangerous. I will end the demo with several defence mechanisms by performing forensics analysis on Phirautee using publicly available tools.
Phirautee
A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written purely using PowerShell and does not require any third-party libraries. This tool steals the information, holds an organisation’s data to hostage for payments or permanently encrypts/deletes the organisation data.
Phirautee is a Living off the Land (LotL) ransomware which means it utilises legit powershell commands and operations to work against the operating system.

Phirautee Introduction
- Phirautee is a proof of concept ransomware tool written purely using PowerShell.
- It uses Living off the Land (LotL) commands to work against the operating system to encrypt files on the machine.
- This tool can be used during internal infrastructure penetration testing or during the red team exercise to validate Blue Team/SOC response to ransom attacks.
- It uses public key cryptography to encrypt user content and exfiltrates large files via Google Drive.
- Upon successful attack the ransomware asks for a payment of 0.10 BTC (~1k USD).
- Detection:
- File extension of the encrypted files are changed to “.phirautee”
- Desktop wallpaper of the compromised host is changed with Phirautee background
- Desktop will have Phirautee.txt file

Phirautee Attack Setup
- Phishing server and domain to target an organisation.
- Email server to send malicious documents as an attachment to the targeted user.
- Macro embedded file as an attachment to user which pulls the ransomware from the remote server to targeted machine and runs it in a memory.
- Modify couple of parameters in the ransomware file to utilise it for your use case.
- For data exfiltration:
- Throwaway Gmail account
- Gmail API access to a throwaway Google Drive
- Setup web application on the Google
Steps for setting up Data Exfiltration using Google Drive
Google offers a REST API that can be accessed via PowerShell to perform operations on the files such as upload, download and delete. The REST API allows you to leverage Google Drive storage from within your app.

Please follow below steps to perform exfiltration via phirautee ransomware.
Step 1: Visit https://console.cloud.google.com/cloud-resource-manager
Step 2: Click on “CREATE PROJECT”

Step 3: Once the project is created enable the Google Drive API by click on the “ENABLE APIS AND SERVICES”.

Step 4: Locate the Google Drive related APIs in the API Library:

Step 5: Once located enable the API. This would allow access to various operations via Google Drive.

Step 6: After enabling the API access click on the “create credentials” button.

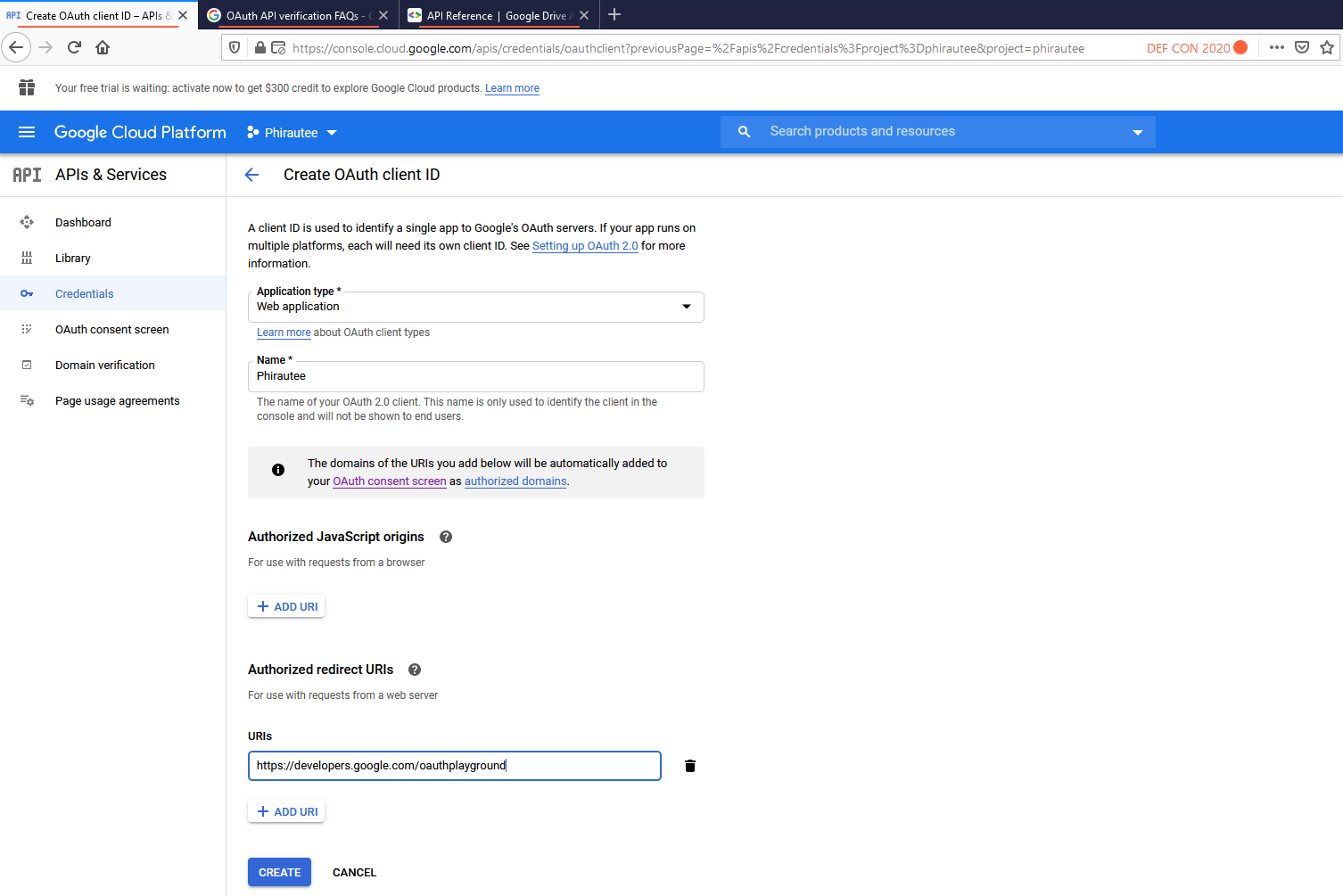
Step 7: Now create OAuth Client ID Credentials

Step 8: Select Web Application as product type and configure the authorized redirect URI to https://developers.google.com/oauthplayground
Step 9: Save your client ID and Secret. If you dont this can always be accessed from credentials in APIs & Services. Now browse to https://developers.google.com/oauthplayground
Step 10: Click on the gear icon and tick on the “Use your own OAuth credentials”

Step 11: Authorize the https://www.googleapis.com/auth/drive API and then Click “Exchange authorization code for tokens”. This should give you 200 OK in the response. Make sure you save your refresh access token. We will need this in the Phirautee to upload large files to the throwaway Google account.


Use of Symmetric Keys & Anonymous SMTP Service
- Phirautee uses two unique symmetric keys
- One for the private key of the certificate that’s being generated on the user machine.
- The other one for uploading exfiltrated data on Google Drive
- The private keys are sent to Pokemail as a zip encrypted files.
- Phirautee uses Pokemail services to distribute the attack infrastructure by creating a random location based email address.


- Uses 2048 bits RSA key to encrypt files on the infected machine.
- Private key of the certificate gets sent to attacker using a pre-shared secret aka symmetric keys.
IoCs for Phirautee
File paths:
C:\temp\cert.cer
c:\temp\sys.txt
c:\temp\backup.zip
c:\temp\sys1.txt
c:\temp\steal.zip
C:\users\$env:USERNAME\PhirauteeBackground-3.jpg
MD5s:
77EA9D33D144072F7B35C10691124D16
4E123FF3A7833F0C8AC6F749D337444D
Domains used for exfil:
https://smtp.pokemail.net
https://www.googleapis.com
https://accounts.google.com
https://raw.githubusercontent.com
Registry files:
HKCU:\Control Panel\DesktopMitigation Strategies
- Network segmentation and detection of lateral movement. Follow principle of least privilege access or restrict access to sensitive servers. Make use of MFA on all important portals.
- Disable PowerShell for standard domain users and perform application whitelisting.
- Frequent network wide backups (if possible offline).
- Apply patches and have a vulnerability management program.
- Have a dedicated incident response team and develop a plan for ransomware events.
- Invest in a good IDS/IPS/EDR/AV/CASB product.
- Validate the effectiveness of your defense tools and technologies through pre-approved offensive exercise.
- Organise phishing and user education training sessions for your employees.
- Have cyber insurance to help cover costs in case you need to pay the ransom. Furthermore, get your insurance policies reviewed to make sure there are no holes.
- Take help from local feds for the decryption keys.
Written by: va-user
Tagged as: internet, ransomware, security, trojan, virus, cyber security alert.
COPYRIGHT 2022 PREEMPTIVE CYBER SECURITY